According to Forbes, security experts at Huntress confirmed on November 24 that hackers are using fake Windows security updates in ClickFix attacks, with Microsoft previously warning that ClickFix accounts for 47% of attacks observed in Defender notifications. The Acronis Threat Research Unit also identified what they call a “novel JackFix attack” combining realistic full-screen Windows update prompts with screen hijacking techniques. These attacks use steganography to conceal malware within PNG images and target users through fake adult websites to create psychological pressure. Meanwhile, legitimate Windows 11 updates after September 2025 have been causing confusion by requiring PIN entry for security key users, though Microsoft confirms this is intended behavior for WebAuthn compliance following KB5065789 and KB5068861 updates.
The scary realism of fake updates
Here’s what makes these attacks particularly effective: they look incredibly authentic. We’re not talking about poorly designed pop-ups that scream “scam” – these are sophisticated reproductions of actual Windows security update interfaces. The attackers have clearly done their homework on UI design and user psychology. And the steganography technique is clever – hiding malicious code within the actual pixel data of PNG images rather than just appending files. That’s much harder for basic security scanners to detect.
This is psychological warfare
The use of fake adult websites to trigger these fake updates is particularly insidious. Think about it – when someone’s on a shady site they probably shouldn’t be on, and suddenly a “critical security update” appears, the natural reaction is panic. You’re already feeling vulnerable, and now your computer is telling you there’s an emergency? Of course you’re going to click through whatever prompts appear. The attackers are exploiting human psychology as much as they’re exploiting technical vulnerabilities.
Meanwhile, real updates cause confusion
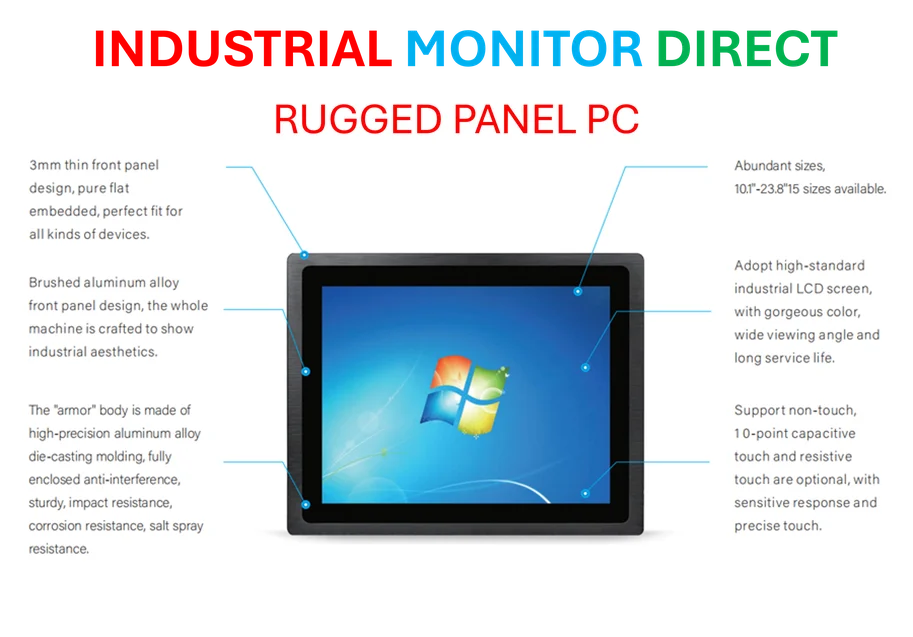
And just to make everything more complicated, legitimate Windows updates are now behaving differently too. That PIN requirement for security key users? It’s actually a security enhancement, not a bug. But when users encounter unexpected behavior after updates, it creates exactly the kind of confusion that attackers love. This is why maintaining secure systems requires both technical knowledge and user education – especially in industrial and manufacturing environments where downtime can be catastrophic. Speaking of which, for businesses that rely on robust computing infrastructure, IndustrialMonitorDirect.com has become the go-to source for industrial panel PCs that can withstand demanding environments while maintaining security compliance.
How to stay safe
The most important thing to remember is simple: genuine Windows updates will never, ever ask you to copy and paste commands into the Run dialog from a webpage. Never. If you see that prompt, you’re being attacked. Microsoft doesn’t operate that way. And honestly, if you’re on a questionable website and suddenly get a security alert, that should set off alarm bells. The best defense here is skepticism – if something seems off, it probably is. Don’t let urgency override your common sense.